- Getting Started
-
Administration Guide
- Get Started with Administering Wyn Enterprise
- Configuration Settings
- Account Management
- Security Management
- System Management
- Document Management
-
How To and Troubleshooting
- Change Default Password
- Set Language Preference
- Slack Integration
- MS Teams Integration
- Create Custom Language Packages
- Configure Identity Server
- Configure Single Sign-on
- Convert Crystal Reports/MS Access Reports to Wyn Reports
- Encrypt or Decrypt Connection Strings
- Using ClickHouse as OLAP Database
- Hide Download Link in Scheduled Tasks
- Configure Redis Cluster using Username and Password
- User Guide
- Developer Guide
Amazon Cognito Service
Amazon Cognito is a customer identity and access management (CIAM) service. Amazon Cognito provides user pool and identity pool to support SSO based access to the Wyn Enterprise application. User pool is a user directory using which users can sign in to the Wyn Enterprise application through Amazon Cognito. Identity pool is used to provide AWS (Amazon Web Services) credentials to the users. To support OAuth authentication, Amazon Cognito provides an OAuth 2 authentication server for token handling and authenticated user management. For more information, see the Using Amazon Cognito hosted UI help article.
Before configuring, ensure the following,
Install the Wyn Enterprise application version 6.0 or above.
Create an application client in the user pool of Amazon Cognito. To create the application client, follow the below instructions,
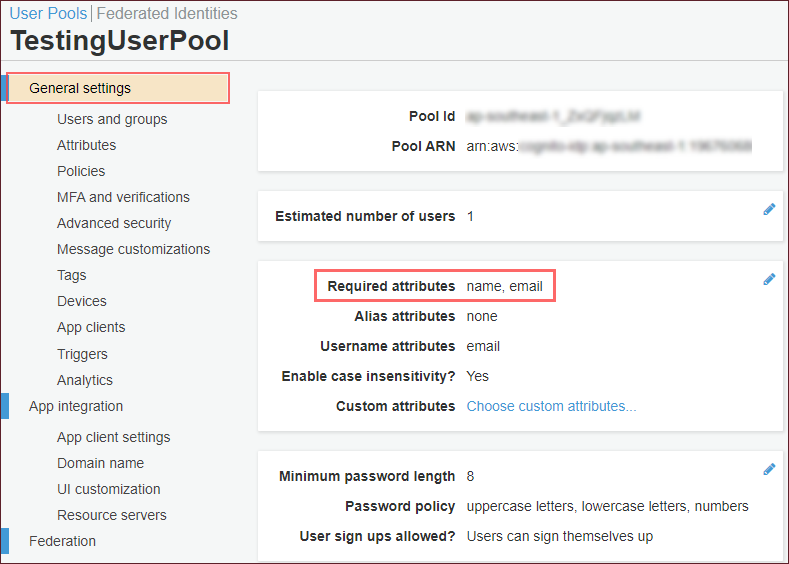
i) Create a User Pool - The Required Attributes should contain name and a valid email. For more information, see the Create a User Pool - Amazon Cognito help article.
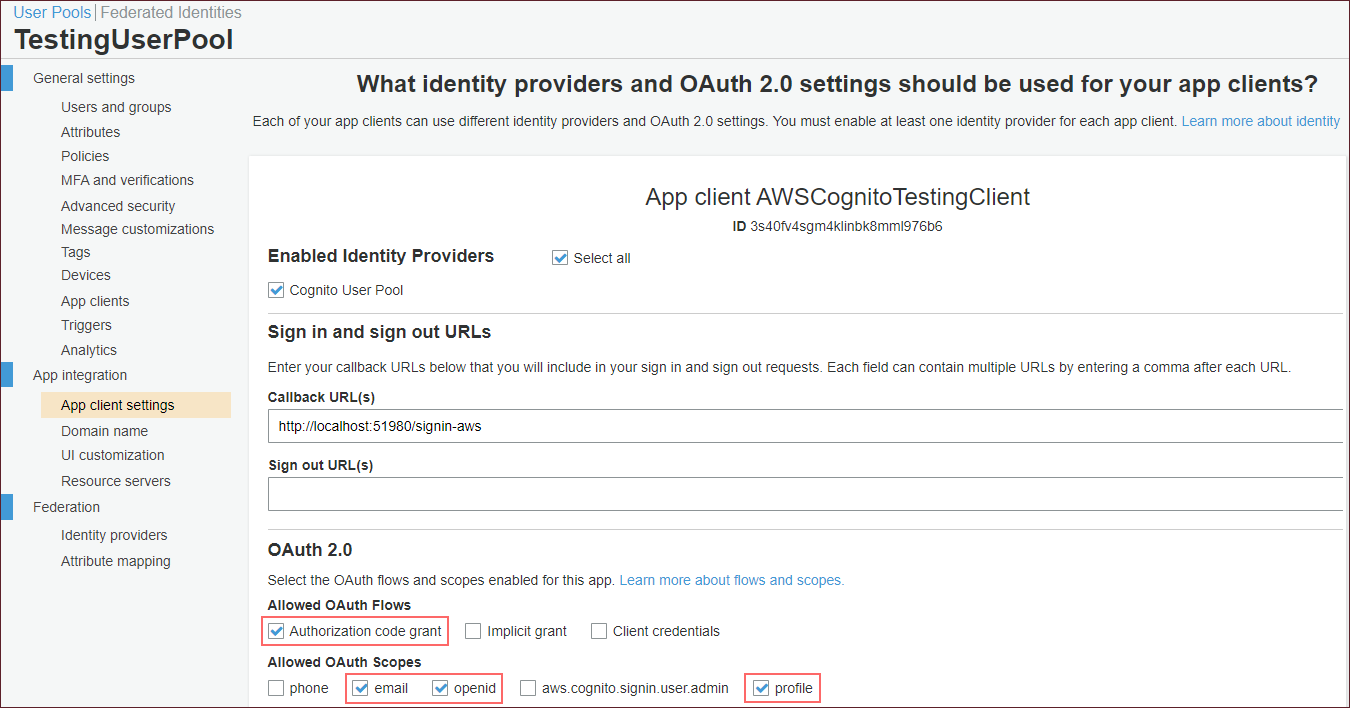
ii) Add an app client - For Allowed OAuth Flows select the Authorization code grant option and, for the Allowed OAuth Scopes select the openid, profile, and email options. For more information, see the Add an app client and set up the hosted UI - Amazon Cognito help article.
Follow the below instructions to configure SSO with Amazon Cognito Service,
Configuration Node Management
Add the SSO configuration node to the Wyn configuration file, Wyn.conf, and ensure the following,
AuthenticationProtocol option must be OIDC.
Scheme is optional. In case, you don't specify the Scheme option in the configuration file, the value of this option will be set to OpenIdConnect, by default.
Authority, ClientId, and ClientSecret options are mandatory and are available in your user pool.
CallbackPath is optional and if not specified, the default value of this option is /signin-oidc. Ensure that theCallbackPath matches the Redirect URI you specified in the app client settings.
<Server> <Authentication> <SSO> <AuthenticationProtocol>OIDC</AuthenticationProtocol> <Scheme>AWS</Scheme> <Authority>https://cognito-idp.{region}.amazonaws.com/{user_pool_id}</Authority> <ClientId>{your_client_id}</ClientId> <ClientSecret>{your_client_secret}</ClientSecret> <CallbackPath>/signin-aws</CallbackPath> <ResponseType>code</ResponseType> <Scopes> <sys:string>openid</sys:string> <sys:string>profile</sys:string> <sys:string>email</sys:string> </Scopes> <ClaimMappings> <sys:Item> <Key>sub</Key> <Value>sub</Value> </sys:Item> <sys:Item> <Key>name</Key> <Value>name</Value> </sys:Item> <sys:Item> <Key>given_name</Key> <Value>given_name</Value> </sys:Item> <sys:Item> <Key>family_name</Key> <Value>family_name</Value> </sys:Item> <sys:Item> <Key>email</Key> <Value>email</Value> </sys:Item> </ClaimMappings> </SSO> </Authentication> </Server>
See the Additional SSO Settings section of the Configure Single sign-on help doc for information on configuring the cookies and incognizant user login options.
Note the following,
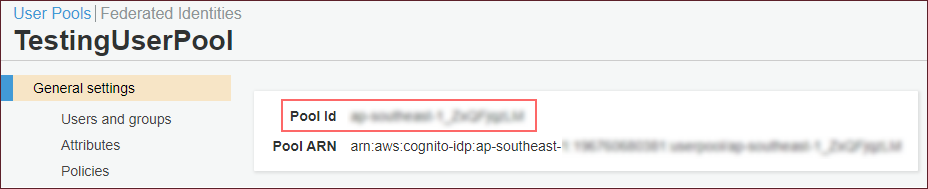
User Pool ID can be found in the General Settings of your user pool.
Region can be found in the URL of your User Pool Management page.